With the release of iOS and iPadOS 14.3, all app updates in the App Store are now required to include Privacy Details, or “nutrition labels”.
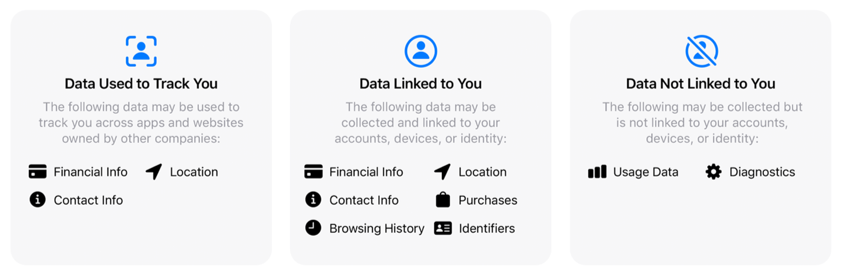
At a high level, there are three categories of nutrition label:
- Data Used to Track You
- “May be used to track you across apps and websites owned by other companies”
- Data Linked to You
- “May be collected and linked to your identity”
- Data Not Linked to You
- “May be collected but it is not linked to your identity”
Within each category, there is additional info split into types of data collected and ways data is used.
Types of data an app can collect includes:
- contact info
- health & fitness
- financial info
- location
- sensitive info
- contacts
- user content
- browsing history
- search history
- identifiers
- purchases
- usage data
- diagnostics
- other data
Ways data is used include:
- third-party advertising
- developer’s advertising or marketing
- analytics
- product personalization
- app functionality
- other purposes
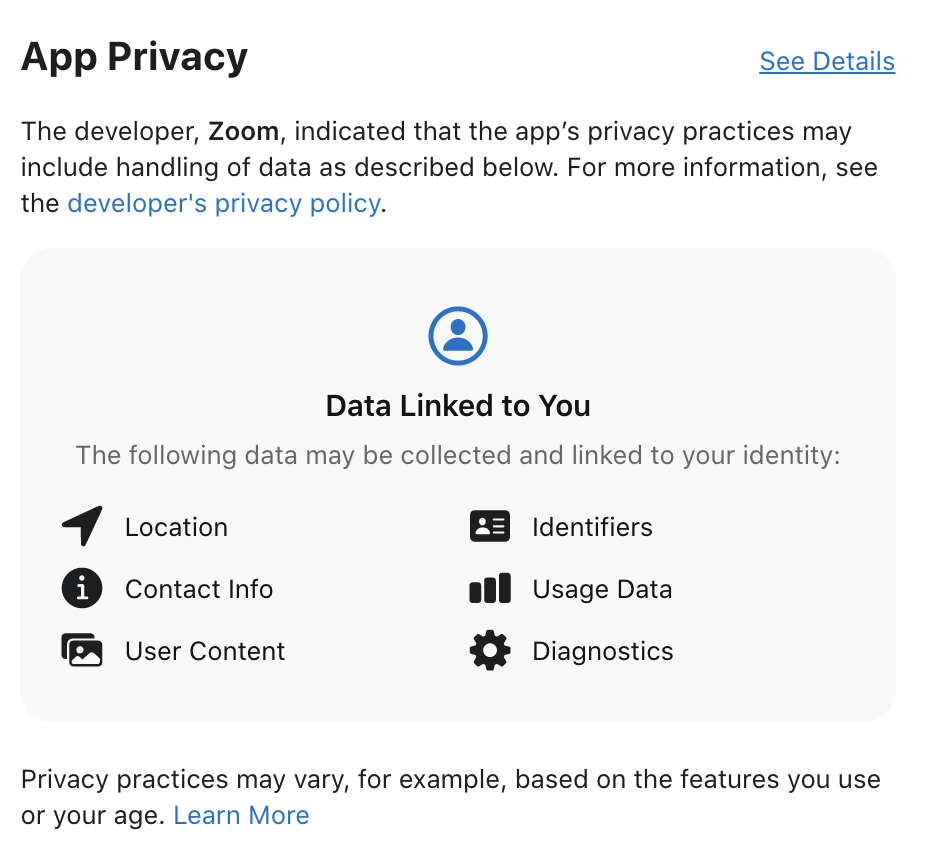
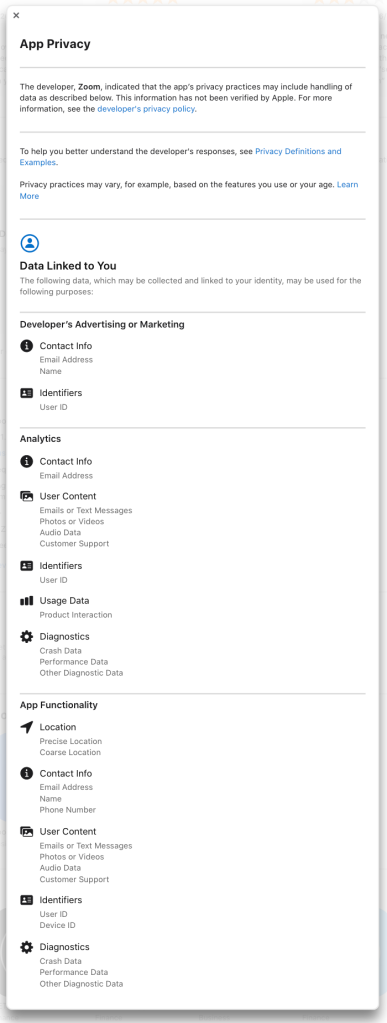
Putting it all together, when looking at an app in the store, like Zoom for example, you can see the app collects your location, contact info, user content, identifiers, usage data, and diagnostics and links the data to you. If this data was in the “not linked to you” category, the data would still be collected, but done so anonymously.
The top level information tells you what data the app collects, but to see how the data is used, you need to select the “See Details” link at the top right of the App Privacy section.
From the expanded view, you can see that Zoom collects data for advertising & marketing, analytics, and general app functionality. This may look like a lot, but Zoom’s data use is comparatively short. Details for Facebook’s data use scroll for days.
And the distinction between data collection and data use is important. For example, an app may collect your location and use it to tell you the weather nearby. Granting permission to location would make sense if you are downloading a weather app. But an app may also collect your location and use it to tell ad providers all the places you go. In this case, giving access to your location would be sketchy if you were downloading a calculator app.
There is also an inherent level of trust associated with Apple’s new model for privacy details, as for app developers:
“You’re responsible for keeping your responses accurate and up to date.”
This means, to apply these new privacy labels, app developers must self report their data use when submitting updates to the app store. Apple does not read through all the code or monitor network traffic to automatically create an app’s privacy details.
Apps can change their behavior with any update, but developers are required to update on their own. App reviewers do not flag when the privacy details need an update.
So while the longevity and robustness of the new privacy nutrition labels remains to be seen, we can take a look at how the most popular apps of 2020 report their privacy nutrition details.
Top 2020 Apps
If you have updated to iOS 14.3, it’s interesting to flip through some of the apps you use to see how they report their data collection and use. Although, it’s not exactly easy to compare two apps.
Since Apple recently unveiled the top games and apps of 2020, you can look at all the privacy nutrition label details in search of trends from the apps everyone are using.
So I did. And compiled the Privacy Nutrition Label Data for the Top Apps of 2020.
This starts off with general info regarding what data is collected, then looks at how specific apps and games report data use, and finally lists insights and questions from the investigation. (All the spreadsheets and data are included at the end).
Nutrition Label Data
General statistics
- 80 total apps
- 20 free apps
- 20 paid apps
- 20 free games
- 20 paid games
- 51 updated to report privacy data
- 32 apps
- 19 games
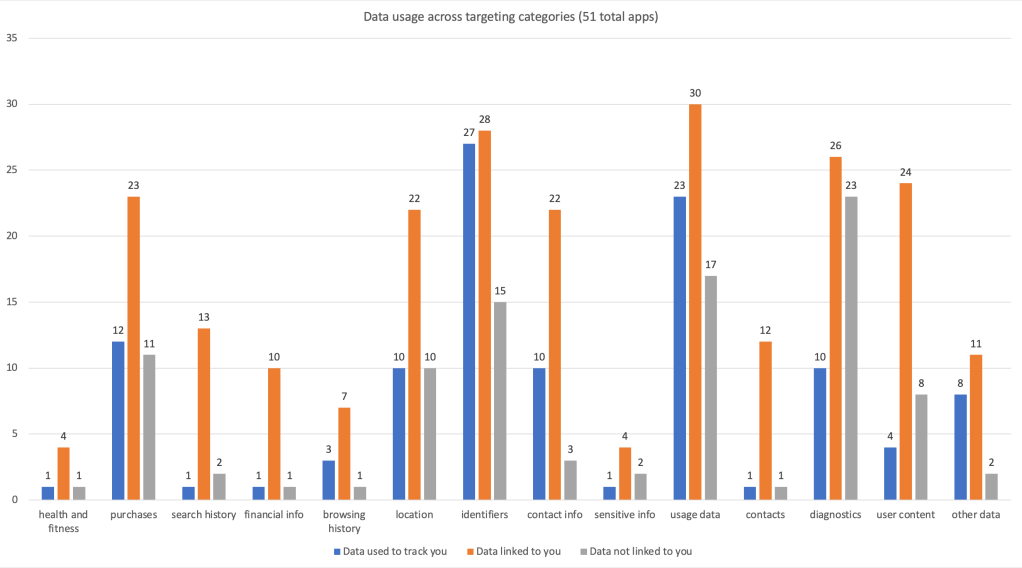
- Top collected data types across all three categories
- identifiers (70)
- usage data (70)
- diagnostics (59)
- purchases (46)
- location (42)
- user content (36)
- contact info (35)
- other data (21)
- search history (16)
- contacts (14)
- financial info (12)
- browsing history (11)
- sensitive info (7)
- health and fitness (6)
- Top collected data types (used to track you)
- identifiers (27)
- usage data (23)
- purchases (12)
- contact info (10)
- diagnostics (10)
- location (10)
- other data (8)
- user content (4)
- browsing history (3)
- contacts (1)
- financial info (1)
- health and fitness (1)
- search history (1)
- sensitive info (1)
- Top collected data types (linked to you)
- usage data (30)
- identifiers (28)
- diagnostics (26)
- user content (24)
- purchases (23)
- location (22)
- contact info (22)
- search history (13)
- contacts (12)
- other data (11)
- financial info (10)
- browsing history (7)
- health and fitness (4)
- sensitive info (4)
- Top collected data types (not linked to you)
- diagnostics (23)
- usage data (17)
- identifiers (15)
- purchases (11)
- location (10)
- user content (8)
- contact info (3)
- sensitive info (2)
- search history (2)
- other data (2)
- health and fitness (1)
- financial info (1)
- contacts (1)
- browsing history (1)
By Apps and Games
- Most types of data collection (17)
- Spotify
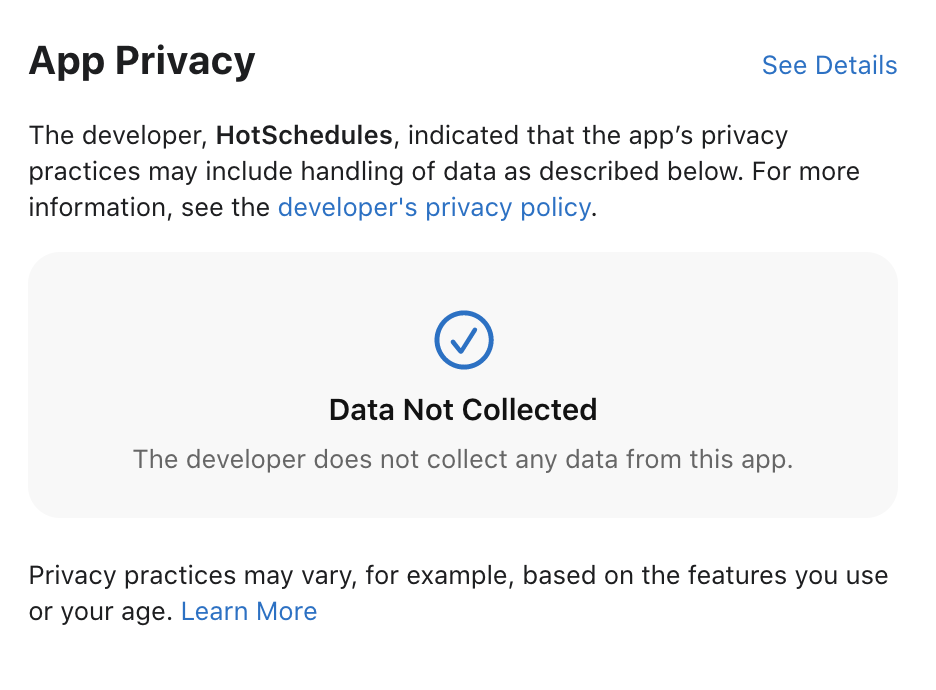
- No data collection (* these are all paid apps/games)
- HotSchedules
- AutoSleep Track Sleep on Watch
- Shadowrocket
- EpocCam Webcamera for Computer
- Arcadia – Arcade Watch Games
- Only collects data not linked to you
- Widgetsmith
- Among Us!
- Most data types used to track you
- Twitter (7)
- Subway Surfers (6)
- Spotify (5)
Free vs Paid
- Average types of data collected (overall)
- Free (10.5)
- Paid (3.6)
- Median types of data collected (overall)
- Free (10)
- Paid (4)
- Average types of data (used to track you)
- Free (2.9)
- Paid (0.3)
- Average types of data (linked to you)
- Free (6.3)
- Paid (1.1)
- Average types of data (not linked to you)
- Free (1.3)
- Paid (2.2)
Insights and Questions
Many of these points stem from the descriptions of Types of data and Data use sections of Apple’s privacy details page.
Free apps
On Apple’s categories:
- “Identifiers” is a vague name, but it’s related to device and user IDs. These types of IDs are often static and used to link your information across apps and services
- “User content” from apps not creating user content is interesting (Disney Plus and Netflix). Guessing these are related to the “Customer Support” category.
- And how does an app have “User Content” not linked to you?
- “Purchases” is not included by Netflix (as you can’t subscribe in the app)
On companies:
- Google hasn’t updated info for any of their apps yet
- Widgetsmith was a breakout iOS 14 app of the year. It only collects anonymous purchase and diagnostic data.
- WhatsApp is Facebook’s least offensive app.
- What is Spotify doing with browsing history?
- Twitter is doing a lot of tracking
On trends:
- “Data linked to you” is largest category and shows most first party data use
- “Data used to track you” is “owned by other companies”
- Companies should move usage data and diagnostics collection from “linked” to “not linked” categories
- Free games do a somewhat better job collecting anonymous data (but also use the same data types to track you)
- Top free apps do less data sharing (tracking) than expected
Overall, rules are new, so companies are still getting used to the categories. Guessing they’ve over-reported as it is easier to move to a more private usage category. Companies may interpret rules differently (Twitter vs Facebook vs TikTok, why so different?)
Free games
- “Identifiers” can be collected but not linked to you?
- Free games do a lot of tracking
- Wondering what the Facebook SDK requires
- Among Us only has anonymous data collection
- Lots of free games need link location to you identity for some reason
Paid apps
- Top paid apps do less tracking and data collection overall
- Also have most non-updated apps in the top 2020 list
- “Data Not Collected” is a tag (took going through a lot of apps to find that out…)
Paid games
- Very few top games have updated
- Seems Facebook SDK could require Identifiers, location, usage data, diagnostics
Overall
- Apple, what’s up with the random ordering of data types? Seems to be consistent by count, but not across all apps
- Health and fitness apps were not very popular this year
- How do changes to data collection and use get reported? Is there a notification added to the nutrition label?
Wrap up
Probably can do a lot more analysis on all this data, but it’s the holidays and everyone is asking me why I’m working. So I’ll leave it at that. As more apps update with their privacy nutrition details, we can expect to learn more about about how the apps we use use our data, and how Apple’s new system changes with time.
Charts and Graphs
Here is all the raw data if you want to compare: Top 2020 Apps – Privacy Summary
☃️ 🛷 ❄️