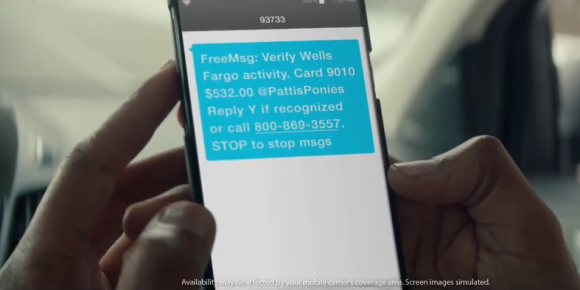
Lots of weird things just happened at once.
It’s always important to be cognizant of what and who you interact with online, but phishing is way up right now, so be extra careful with emails, links, and articles sent to you that you didn’t initiate or request. And while email phishing is often a main focus for scams, there are additional methods to be aware of and keep in mind. Reseller and rental sites like eBay, Craigslist and Airbnb present similar opportunities for scams, however these scams are crafted differently since you are often the one initiating the contact with an unverified third party (instead of the other way around).
So weirdness, here’s what happened
Over the course of the afternoon, 5 phishy things happened to three different groups of people I know.
- Three people in the same family individually received notices that a PayPal, credit card, and Instagram account were hacked.
- A friend got an email that someone signed into their Instagram on a new device.
- Another fiend stumbled across a Craigslist apartment rental phishing scheme. (The exact one covered in this report. Word for word, save for a change in company name and a different person in nearly identical photos)
This very coincidental timing, but it’s a good opportunity for an internet safety refresher!
Safety tips & reminders:
I shared these with family and friends after all this weirdness, but will aggregate them here.
1. When in doubt, go to the actual site
If you get an email from PayPal (or your bank or Instagram) about an account issue, go to the PayPal website yourself to check out the notification. Don’t click on any links sent to you. You can hover over links to see where they really go, but even then, it can be easy to miss smaII deta1ls.

So to be safe, go to PayPal using the app, by searching for PayPal (trusting the wisdom of the search engine crowd), or by manually going to https://www.paypal.com.
Better yet once your are on the PayPal.com that you know is the actual PayPal.com, add it to your favorites and use your own personal trusted bookmark to get back to the real PayPal every time. This way you don’t make a mistake later by mistyping the url and ending somewhere you don’t expect. (And yes, I’m purposefully not linking to PayPal from here. Go build that muscle)
This tip applies to phone calls too!
Summary: It’s your best bet to search for the site/article/etc or go directly to the url if you have it saved somewhere.
2. Use a password manager
You can visit every site you go to as carefully as possible, but if you reuse passwords, one security breach can cause issues across your accounts.
A password manager creates strong, unique passwords for every one of your accounts and securely keeps track of them all for you. You only need to remember your master password to unlock the account.
Some good options are LastPass, Dashlane, and 1Password.
They can also help you more easily change passwords if one is stolen or part of a data breach. You can check to see if your accounts have been part of a data breach using Have I Been Pwned (just don’t enter your current passwords).
Password managers can be difficult to transition to at first, as you need to manually change passwords one at a time, but if you use a password manager solely to keep track of new accounts, you can quickly start to see the benefit.
Read this exhaustive post to learn more before you set up a password manager. A quote:
Password managers are programs that remember passwords for you, along with the email address or other user identifier you use for each account. They make it easier to use strong passwords: those that are sufficiently random, long, and different for every one of your accounts. They also make it easier to lose all your passwords at once, or for attackers to steal all your passwords in one instant.
Summary: See above quote, but you should probably be using one of these.
3. Set up two factor authentication (2FA)
After setting up strong passwords, you can go a step further to safeguard that even if one of your account credentials is compromised, you are still in control of signing into the account.
Two factor authentication satisfies the “something you know, something you have” paradigm for online security (or the first two parts of multi-factor authentication). You know your password and have either a code or USB key or app to verify you are you. If your password is compromised, the second factor of authentication ensures someone with just your password cannot log in.
Needing a second factor can cause problems, however, if you (who is in reality, is you) loses the second factor of authentication. Then you can be locked out just as if you were an attacker.
Also, if multiple people use the same account, two factor authentication can be difficult. With 2FA enabled someone may try to log into an account and the 2FA code can be sent so someone else (which also happened to my family today).
Read this other equally exhaustive post to learn more before you set up 2FA.
Summary: Two factor auth can help keep your accounts secure, but comes with some extra challenges.
4. Keep third party communication within app and website services
This one is related to staying safe when reaching out to others you don’t know online. Talking to strangers! 😱
Whenever possible, keep communication within the app or website service you are using. If buying on eBay, communicate on eBay. If renting on Airbnb, use their chat functionality. Let the site intermediate communication. Don’t share your email or phone number to talk with a third party seller or host outside of the service. Major sites like eBay and Airbnb have measures in place to help you stay safe (and allow you to provide evidence in case of an issue), but only if you leverage their tools.
Be extra cognizant on Craigslist where direct email communication is the standard! I’ll put this Anatomy of a rental phishing scam post here again as a reminder to read it. A quote:
The first red flag was “So we’ll keep our communication to email if that’s ok with you”.
This tip also applied to articles you read or videos you watch. If you aren’t sure of the source, don’t trust, verify 🙃
Summary: There are more signs of a scam than only asking for your bank account and credit card information.
5. Bonus Tip: Use Zoom on your phone or browser
If you use Zoom, you should know that Google banned it’s employees from using the desktop app, and suggests to use mobile or web.
Employees who have been using Zoom to stay in touch with family and friends can continue to do so through a web browser or via mobile
Google’s guidance is to uninstall and block the app completely (maybe because they prefer everyone to use Hangouts 🤷♂️). In any case, if you’re interested, here’s how you can uninstall the desktop version on Mac and PC.
A legitimate reason behind allowing mobile and web, but blocking desktop, stems from the fact that mobile and web platforms have security and containment measures in place that limit sites and apps from accessing your underlying device. Whereas apps installed from the internet can do whatever they want after you type in your computer account password to allow higher level device access.
To continue using Zoom on a desktop, here’s Zoom’s support article on how to join a call using your web browser. The link is a bit hidden (and misleading), but it looks like this:
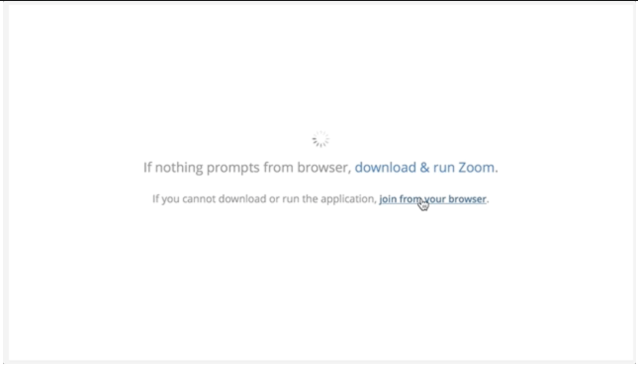
Summary: Use your phone to show off your Zoom backgrounds
That’s all for now
Stay safe. Wash your hands. Wear a mask. Don’t touch your face or click on links in your email 🧼